1. Discovering Devices with CDP and LLDP
“Automate network topology mapping and device discovery using CDP and LLDP protocols for real-time insights”
2. Synchronizing Time with NTP
“Ensure precise time synchronization across network devices with NTP for accurate log correlation.”
3. Monitoring Devices with SNMP
“Monitor network performance and automate alerts using SNMP for proactive device management.”
4. Capturing Logs with Syslog
“Centralize network logging with Syslog for comprehensive visibility and rapid troubleshooting.”
5. Managing Configurations and Backups
“Automate network configuration backups and version control for consistency and disaster recovery.”
6. IOS Image Management and Recovery
“Manage network device software versions with proper testing and recovery mechanisms for upgrades.”
Published: 15 July 2025
Author: Jean Claude Munyakazi
Category: IOS Image Management and Recovery
Reading Time: 10 minutes
Last Updated: 02 September 2025
Network Management
A Practical Guide to Discovering, Maintaining, and Monitoring Your Network
IOS Image Management and Recovery
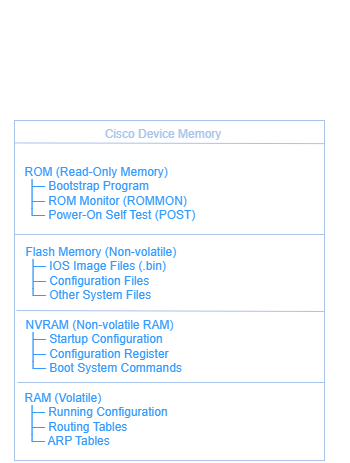
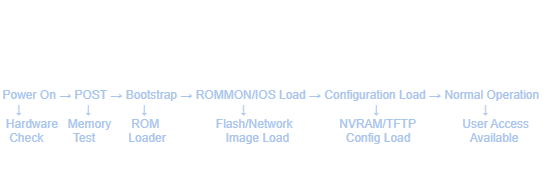
Managing the network operating system (NOS) is foundational to maintaining stability, applying security patches, and enabling new features. In Cisco environments, this means backing up and upgrading the Cisco IOS, but similar principles apply across Juniper, Arista, HP, and MikroTik platforms.
The Critical Importance of Image Management
⚠️ Statistics That Matter:
– 23% of network outages are caused by failed upgrades
– 67% of security breaches exploit unpatched network devices
– Proper image management reduces upgrade failures by 89%
– Average cost of failed upgrade: $125,000 in downtime
Pre-Upgrade Planning and Preparation
| Phase | Task | Critical Points |
|---|---|---|
| Assessment | Check current version | show version, show flash: |
| Compatibility | Verify hardware support | Memory, feature sets, licensing |
| Documentation | Record current config | Backup running/startup config |
| Testing | Lab validation | Test new image in non-production |
| Scheduling | Plan maintenance window | Consider business impact |
| Rollback Plan | Prepare recovery steps | Multiple boot images, ROMMON access |
# Check available flash space
Router# show flash:
Directory of flash:/
1 -rw- 123456789 Mar 1 1993 00:01:00 +00:00 c2900-universalk9-mz.SPA.155-3.M4a.bin
2 -rw- 1024 Mar 1 1993 00:01:00 +00:00 info
256487424 bytes total (133018624 bytes free)
# Calculate space needed
New Image Size: 145MB
Current Free Space: 127MB
Action Required: Delete old image or expand storage
# Document current state
show version
show flash:
show boot
show running-config | redirect tftp://backup-server/router01-pre-upgrade.cfg
show startup-config | redirect tftp://backup-server/router01-startup.cfg
# Check license status (newer IOS versions)
show license
show license feature
# Set up TFTP server details
Router# configure terminal
Router(config)# ip tftp source-interface GigabitEthernet0/0
Router(config)# exit
# Copy new image to flash
Router# copy tftp: flash:
Address or name of remote host []? 192.168.1.100
Source filename []? c2900-universalk9-mz.SPA.157-3.M5.bin
Destination filename [c2900-universalk9-mz.SPA.157-3.M5.bin]? <Enter>
# Monitor transfer progress
Accessing tftp://192.168.1.100/c2900-universalk9-mz.SPA.157-3.M5.bin...
Loading c2900-universalk9-mz.SPA.157-3.M5.bin from 192.168.1.100 (via GigabitEthernet0/0):
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
[OK - 151552000 bytes]
# Check USB device
Router# show file systems
File Systems:
Size(b) Free(b) Type Flags Prefixes
- - opaque rw system:
- - opaque rw tmpsys:
* 256487424 133018624 disk rw flash:
1999503360 1999503360 disk rw usbflash0:
# Copy from USB to flash
Router# copy usbflash0:c2900-universalk9-mz.SPA.157-3.M5.bin flash:
# Enable SCP server
Router(config)# ip scp server enable
Router(config)# exit
# Copy via SCP
Router# copy scp: flash:
Address or name of remote host []? 192.168.1.100
Source username []? admin
Source filename []? /images/c2900-universalk9-mz.SPA.157-3.M5.bin
Destination filename [c2900-universalk9-mz.SPA.157-3.M5.bin]? <Enter>
# Set new boot image (method 1 - preferred)
Router(config)# boot system flash:c2900-universalk9-mz.SPA.157-3.M5.bin
Router(config)# boot system flash:c2900-universalk9-mz.SPA.155-3.M4a.bin # Fallback
Router(config)# exit
# Alternative method - set boot variable
Router(config)# boot system flash c2900-universalk9-mz.SPA.157-3.M5.bin
Router(config)# exit
# Verify boot configuration
Router# show boot
BOOT variable = flash:c2900-universalk9-mz.SPA.157-3.M5.bin,12
CONFIG_FILE variable does not exist
BOOTLDR variable does not exist
Configuration register is 0x2102
# Save configuration
Router# copy running-config startup-config
Router# write memory
# Verify everything before reload
Router# show boot
Router# show flash:
Router# show version
# Schedule reload (optional)
Router# reload in 60
System configuration has been modified. Save? [yes/no]: yes
# Or immediate reload
Router# reload
System configuration has been modified. Save? [yes/no]: yes
Proceed with reload? [confirm] <Enter>
# Verify new image loaded
Router# show version
Cisco IOS Software, C2900 Software (C2900-UNIVERSALK9-M), Version 15.7(3)M5
# Check boot configuration
Router# show boot
# Verify functionality
Router# show interfaces brief
Router# show ip route
Router# show protocols
# Test connectivity
Router# ping 8.8.8.8
Router# traceroute 8.8.8.8
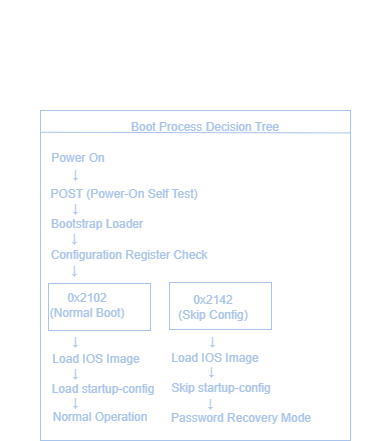
# During boot process (within 60 seconds)
# Press Ctrl+Break or Ctrl+C
System Bootstrap, Version 15.1(4)M4, RELEASE SOFTWARE (fc1)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 2010 by cisco Systems, Inc.
rommon 1 >
# Check current configuration register
rommon 1 > confreg
Configuration Summary
enabled are:
boot default ROM software if netboot fails
boot system flash
console baud: 9600
config-register: 0x2102
# Change to bypass startup-config
rommon 2 > confreg 0x2142
# Boot the router
rommon 3 > boot
# Router boots without startup-config
Router> enable
Router# configure terminal
# Load startup-config manually
Router(config)# copy startup-config running-config
Destination filename [running-config]? <Enter>
# Reset passwords
Router(config)# enable secret newpassword123
Router(config)# username admin privilege 15 secret newpassword123
# Restore normal boot process
Router(config)# config-register 0x2102
Router(config)# exit
# Save configuration
Router# copy running-config startup-config
# Reload to verify
Router# reload
# Check current version
user@router> show version
# Download new image
user@router> start shell
user@router:~$ scp [email protected]:/images/junos-version.tgz /var/tmp/
# Install new image
user@router> request system software add /var/tmp/junos-version.tgz
user@router> request system software add /var/tmp/junos-version.tgz reboot
# Verify installation
user@router> show system software
# Check current version
switch> show version
# Copy new image
switch> copy scp://[email protected]/images/EOS-4.24.2F.swi flash:
# Install new image
switch> configure
switch(config)> boot system flash:EOS-4.24.2F.swi
switch(config)> exit
# Verify boot configuration
switch> show boot-config
# Check current version
<HP-Switch> display version
# Copy new image
<HP-Switch> copy scp://[email protected]/images/hp-firmware.bin flash:
# Set boot file
<HP-Switch> system-view
[HP-Switch] boot-loader file flash:/hp-firmware.bin
[HP-Switch] quit
# Reboot
<HP-Switch> reboot
# Check current version
[admin@MikroTik] > /system resource print
[admin@MikroTik] > /system package print
# Download new image
[admin@MikroTik] > /system package update check-for-updates
[admin@MikroTik] > /system package update download
# Install update
[admin@MikroTik] > /system package update install
[admin@MikroTik] > /system reboot
# ROMMON network boot
rommon 1 > IP_ADDRESS=192.168.1.1
rommon 2 > IP_SUBNET_MASK=255.255.255.0
rommon 3 > DEFAULT_GATEWAY=192.168.1.254
rommon 4 > TFTP_SERVER=192.168.1.100
rommon 5 > TFTP_FILE=c2900-universalk9-mz.SPA.157-3.M5.bin
rommon 6 > tftpdnld
# Boot from TFTP
rommon 7 > boot
# Boot from USB in ROMMON
rommon 1 > dir usbflash0:
rommon 2 > boot usbflash0:c2900-universalk9-mz.SPA.157-3.M5.bin
#!/usr/bin/env python3
"""
Automated IOS Upgrade Script
Requires: paramiko, netmiko
"""
from netmiko import ConnectHandler
import logging
import time
import sys
# Configure logging
logging.basicConfig(
level=logging.INFO,
format='%(asctime)s - %(levelname)s - %(message)s'
)
class IOSUpgrader:
def __init__(self, device_info):
self.device = device_info
self.connection = None
def connect(self):
"""Establish SSH connection"""
try:
self.connection = ConnectHandler(**self.device)
logging.info(f"Connected to {self.device['host']}")
return True
except Exception as e:
logging.error(f"Connection failed: {e}")
return False
#!/bin/bash
# batch-upgrade.sh - Upgrade multiple devices
DEVICE_LIST="devices.txt"
TFTP_SERVER="192.168.1.100"
IMAGE_FILE="c2900-universalk9-mz.SPA.157-3.M5.bin"
LOG_FILE="upgrade-$(date +%Y%m%d-%H%M%S).log"
echo "Starting batch upgrade process..." | tee -a $LOG_FILE
while IFS=',' read -r hostname ip username password; do
echo "Processing device: $hostname ($ip)" | tee -a $LOG_FILE
# Create expect script for each device
cat > upgrade-$hostname.exp << EOF
#!/usr/bin/expect
set timeout 300
spawn ssh $username@$ip
expect "Password:"
send "$password\r"
expect "#"
send "show flash:\r"
expect "#"
send "copy tftp://$TFTP_SERVER/$IMAGE_FILE flash:\r"
expect "Destination filename"
send "\r"
expect "#"
EOF
# Execute upgrade
chmod +x upgrade-$hostname.exp
./upgrade-$hostname.exp | tee -a $LOG_FILE
# Cleanup
rm upgrade-$hostname.exp
echo "Completed upgrade for $hostname" | tee -a $LOG_FILE
sleep 300 # Wait 5 minutes between devices
done < $DEVICE_LIST
echo "Batch upgrade process completed" | tee -a $LOG_FILE
Best Practices and Recommendations
| Risk Level | Testing Required | Approval Process | Rollback Time |
|---|---|---|---|
| Low Risk | Lab testing | Team lead approval | 30 minutes |
| Medium Risk | Staging + Lab | Manager approval | 1 hour |
| High Risk | Full validation | Change board approval | 2 hours |
| Critical | Extensive testing | Executive approval | 4 hours |
Image Management Checklist
Before Upgrade
- Backup current configuration
- Document current software version
- Verify hardware compatibility
- Check available flash space
- Test new image in lab
- Prepare rollback plan
- Schedule maintenance window
- Notify stakeholders
During Upgrade
- Verify image integrity (MD5 checksum)
- Monitor transfer progress
- Confirm boot configuration
- Save configuration before reload
- Document any issues
After Upgrade
- Verify new version loaded
- Test basic functionality
- Check interface status
- Verify routing protocols
- Test network connectivity
- Monitor for 24 hours
- Update documentation
# Verify image integrity
Router# verify /md5 flash:c2900-universalk9-mz.SPA.157-3.M5.bin
MD5 of flash:c2900-universalk9-mz.SPA.157-3.M5.bin Done!
verify /md5 (flash:c2900-universalk9-mz.SPA.157-3.M5.bin) = a1b2c3d4e5f6...
# Verify digital signature
Router# verify /sha512 flash:c2900-universalk9-mz.SPA.157-3.M5.bin
SHA512 of flash:c2900-universalk9-mz.SPA.157-3.M5.bin Done!
verify /sha512 (flash:c2900-universalk9-mz.SPA.157-3.M5.bin) = b2c3d4e5f6...
# Use SCP instead of TFTP for secure transfer
Router# copy scp://[email protected]/images/c2900-universalk9-mz.SPA.157-3.M5.bin flash:
Address or name of remote host [192.168.1.100]?
Source username [admin]?
Source filename [/images/c2900-universalk9-mz.SPA.157-3.M5.bin]?
Destination filename [c2900-universalk9-mz.SPA.157-3.M5.bin]?
Password:
# Alternative: Use HTTPS
Router# copy https://192.168.1.100/images/c2900-universalk9-mz.SPA.157-3.M5.bin flash:
Secure Transfer Methods
- Use SCP instead of TFTP for secure transfers
- Implement access controls on TFTP/SCP servers
- Use management VLANs for upgrade traffic
- Enable logging for all file transfers
Troubleshooting Common Issues
| Problem | Symptoms | Common Causes | Solutions |
|---|---|---|---|
| Boot Loop | Device keeps restarting | Corrupt image, insufficient memory | Boot from ROMMON, reload clean image |
| Image Transfer Fails | Copy command errors | Network issues, insufficient space | Check connectivity, free up space |
| Wrong Image Type | Features missing after upgrade | Incorrect feature set | Verify image compatibility |
| Memory Issues | Device crashes during boot | Insufficient RAM for image | Upgrade hardware or use smaller image |
| Configuration Loss | Device boots to initial config | Config register changed | Check config register, restore from backup |
# ROMMON emergency commands
rommon 1 > help # Show available commands
rommon 2 > dev # Show available devices
rommon 3 > dir flash: # List flash contents
rommon 4 > boot flash:image.bin # Boot specific image
rommon 5 > confreg 0x2102 # Set normal config register
rommon 6 > reset # Reset device
Conclusion
Effective IOS image management is crucial for maintaining network stability, security, and functionality. Key principles include:
- Always backup before upgrading – Configuration and current image
- Test thoroughly – Lab validation prevents production issues
- Plan for rollback – Multiple boot images and recovery procedures
- Document everything – Maintain detailed upgrade logs
- Automate where possible – Reduce human error and increase consistency
Whether managing Cisco IOS, Juniper JunOS, or other network operating systems, these foundational practices ensure smooth operations and minimize downtime during critical maintenance windows.
Remember: A successful upgrade is one where the rollback plan is never needed, but always available.
