IT Security Management Framework
Understanding the ISO Cybersecurity Model: A Framework for Information Security Management
In an increasingly connected world, information security has become a complex and critical function in every organization. Just as the OSI model guides network engineers, the ISO/IEC cybersecurity model provides structure and clarity for cybersecurity professionals striving to secure data and digital assets.
This blog introduces the ISO/IEC 27000 series, a globally recognized framework for implementing an Information Security Management System (ISMS). Whether new to cybersecurity or working toward ISO 27001 compliance, understanding this framework is essential for aligning technical safeguards with business priorities.
What Is the ISO Cybersecurity Model?
The ISO/IEC 27001 standard, first published in 2005 and most recently revised in 2022, offers a comprehensive framework for information security management. The latest revision represents a significant evolution from previous versions, streamlining the approach while maintaining robust security coverage.
Unlike hierarchical models, the ISO framework treats all security domains as interconnected components of a holistic security strategy. This peer-based approach ensures that no single area of security is prioritized over others, creating a balanced and comprehensive protection strategy.
The Modern 4-Domain Structure (ISO 27001:2022)
The current ISO 27001 standard organizes security controls into four primary domains, representing a major simplification from the previous 14 control categories used in the 2013 version. This streamlined approach reduces the total number of controls from 114 to 93, making implementation more manageable while maintaining comprehensive security coverage.
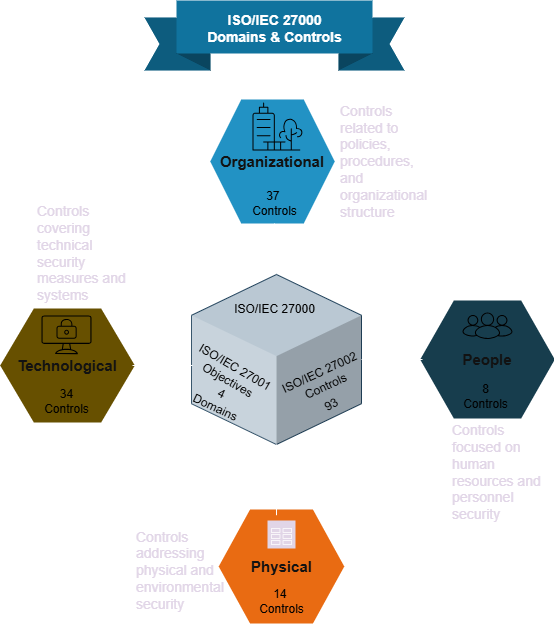
1. Organizational Controls
These controls establish the governance foundation for information security, covering policies, procedures, risk management, and organizational structure. This domain ensures that security is embedded into the fabric of how an organization operates and makes decisions. It includes elements previously found in areas like security policy, compliance, and business continuity management.
2. People Controls
Focused on human resources security, this domain addresses personnel-related risks and security measures. It covers everything from security awareness training and background checks to secure termination processes and access management for employees and contractors. This consolidates what was previously spread across human resources security and access control domains.
3. Physical Controls
This domain encompasses physical and environmental security measures that protect information assets from physical threats. It includes facility security, equipment protection, secure disposal of assets, and environmental controls that ensure business continuity.
4. Technological Controls
Covering technical security measures and systems, this domain addresses the technological aspects of information security. It includes network security, system security, application security, cryptography, and technical access controls. This domain consolidates elements from communications and operations management, information systems development, and technical access controls.
ISO/IEC 27002:2022
Information Security Controls - Complete Structure
ISO/IEC 27002:2022
93 Security Controls
Key Statistics
Control Objectives vs. Controls
The ISO/IEC 27001 standard defines “control objectives” as high-level goals for information security. These objectives form the foundation for organizational policies and audits. For instance:
- “To control access to networks using appropriate authentication mechanisms.”
Meanwhile, ISO/IEC 27002 defines the actual controls that fulfill these objectives. Controls are technical or procedural steps, such as:
- Requiring strong passwords (minimum eight characters, mixed case, symbols).
Controls are flexible guidelines, not rigid rules. They maintain vendor neutrality and allow multiple valid implementation paths, making them practical across diverse environments.
The table below illustrates practical examples of ISO/IEC 27002 control objectives and corresponding controls, organized by the four key themes of information security: Organizational, People, Physical, and Technological. These examples highlight how strategic goals translate into real-world safeguards.
| Theme | Objective | Control |
|---|---|---|
| 5. Organizational Controls | Clause 5.1: Establish a consistent security policy framework. | Develop and approve an information security policy document. |
| Clause 5.12: Ensure appropriate classification of information. | Implement data classification and labeling procedures. | |
| Clause 5.23: Safeguard use of cloud services. | Assess security risks before adopting cloud services. | |
| Clause 5.16: Maintain oversight of operational changes. | Use a formal change management process. | |
| 6. People Controls | Clause 6.1: Minimize risks through responsible hiring. | Conduct background checks before employment. |
| Clause 6.2: Define roles and responsibilities. | Include security terms in employment contracts. | |
| Clause 6.4: Enforce compliance with policies. | Establish and apply a disciplinary process. | |
| Clause 6.6: Maintain confidentiality. | Require signed NDAs for employees and contractors. | |
| 7. Physical Controls | Clause 7.1: Protect secure areas. | Define and enforce physical security perimeters. |
| Clause 7.2: Prevent unauthorized access to facilities. | Use ID badge systems and surveillance. | |
| Clause 7.7: Prevent data leaks from retired equipment. | Shred hard drives before disposal. | |
| Clause 7.9: Maintain confidentiality in secure areas. | Restrict access and enforce clean desk policies. | |
| 8. Technological Controls | Clause 8.1: Protect endpoint devices. | Enforce device encryption and antivirus tools. |
| Clause 8.2: Control privileged access. | Implement RBAC and monitor admin activities. | |
| Clause 8.11: Prevent data leaks. | Mask sensitive fields in logs and exports. | |
| Clause 8.23: Manage web access. | Deploy web filtering to block risky domains. |
Mapping ISO to the CIA Triad
The ISO 27000 series provides a universal cybersecurity framework, but organizations must tailor it to their specific needs. The key lies in understanding how different businesses prioritize Confidentiality, Integrity, and Availability based on their industry and operations.
Strategic Prioritization by Industry
Google’s Approach: Confidentiality + Availability
Google focuses heavily on protecting user data (confidentiality) while ensuring services remain accessible 24/7 (availability). Since Google doesn’t verify user-generated content, integrity receives less emphasis in their resource allocation.
Amazon’s Strategy: Availability-First
For Amazon, every second of downtime means lost sales. Their primary focus is availability, ensuring customers can always make purchases. While confidentiality remains important for customer trust, availability drives their largest security investments in redundant systems and failover mechanisms.
The Statement of Applicability (SOA)
The SOA document serves as the bridge between the comprehensive ISO framework and your organization’s reality. It:
- Identifies which ISO controls apply to your specific environment
- Maps selected controls to your CIA priorities
- Justifies resource allocation decisions
- Creates a tailored security roadmap
Practical Implementation
Organizations don’t ignore any aspect of the CIA triad; they strategically allocate resources based on business impact:
- High-priority elements receive more controls, monitoring, and investment
- Standard-priority elements maintain baseline protection with optimized resources
- All three elements maintain minimum security standards regardless of prioritization
This approach ensures cybersecurity investments align with business objectives while maintaining comprehensive protection across confidentiality, integrity, and availability.
Applying the ISO Model to Data States
Data exists in three states, and the ISO framework addresses security across all of them:
- In Transit: Managed by network security teams
Ex: secured with TLS, VPNs, and firewall rules
- At Rest: Protected by infrastructure and server teams
Ex: protected via encryption, access restrictions, and backups
- In Use: Secured by application and endpoint teams
Ex: monitored through endpoint protection, DLP tools, and policy enforcement.
ISO 27002 controls apply across these states, with team collaboration ensuring that appropriate safeguards are in place for each data type. For example:
- Network teams ensure secure data transmission.
- Developers safeguard application data integrity.
- Server admins manage access control and backups.
Technical Safeguards and Policy Fulfillment
Upper management sets policy directives, such as requiring encryption for outbound data. IT teams translate these directives into practice using technologies like:
- Firewalls
- VPNs
- Multi-factor authentication
- Biometric systems
The ISO framework provides specific guidance for implementation. For instance, organizational controls define responsibilities such as:
- Allocation of security responsibilities
- Confidentiality agreements
- Independent review of information security
These controls align teams with strategic goals while ensuring compliance and continuous improvement.
ISO in Action: Case Example
- Access control (Technological, Section 8) for patient data
- Incident response (Organizational, Section 5) in case of data breaches
- Physical security (Physical, Section 7) for server rooms
Why the 2022 Revision Matters
The 2022 revision reflects the evolving cybersecurity landscape and addresses modern threats more effectively. Key improvements include:
- Simplified Structure: The reduction from 14 to 4 domains makes the framework more intuitive and easier to navigate
- Enhanced Clarity: Controls are more clearly defined and easier to understand for implementation
- Modern Threat Landscape: Updated controls better address contemporary cybersecurity challenges including cloud security, remote work, and emerging technologies
- Improved Alignment: Better integration with other management system standards and business processes
Organizations have until October 2025 to transition from the 2013 version to the new standard, allowing time for careful planning and implementation.
Final Thoughts: Why ISO/IEC 27000 Matters
- Standardize and structure their security efforts
- Align security practices with regulatory and operational goals
- Build trust with clients, partners, and auditors
- Create a comprehensive security program that addresses modern threats
Whether pursuing formal certification or simply improving your security posture, the ISO model serves as a powerful roadmap for protecting digital assets in today’s complex threat landscape.
In cybersecurity, structure equals strength. The ISO/IEC 27001:2022 framework gives us the modern structure we need. The rest is up to us.
Security Management Framework
Key Terms & Concepts ISO/IEC Security Framework
| Term | Definition |
|---|---|
| ISO/IEC 27001 | International standard for establishing, implementing, maintaining, and continually improving an ISMS. |
| ISMS | Information Security Management System, a structured set of policies and controls for managing security. |
| ISO/IEC 27002 | Companion standard providing detailed guidance on the implementation of security controls in ISO 27001. |
| Organizational Controls | Controls related to governance, risk management, policies, and procedures that establish security culture. |
| People Controls | Measures related to HR, employee training, contracts, and responsibilities for managing human risks. |
| Physical Controls | Controls that protect the physical environment, equipment, and media from unauthorized access or damage. |
| Technological Controls | Technical security mechanisms like encryption, access controls, monitoring, and secure software design. |
| Control Objective | A high-level goal such as “ensure only authorized users can access systems.” |
| Control | A specific measure or action taken to meet a control objective (e.g., use of MFA, firewall rules). |
| CIA Triad | Core principles of information security: Confidentiality, Integrity, and Availability. |
| Statement of Applicability (SoA) | A document that maps which ISO controls apply and why, tailored to business risks and needs. |
| Data at Rest | Data stored on physical media (e.g., disks, databases); typically protected through encryption. |
| Data in Transit | Data actively moving through networks; secured via protocols like TLS or VPN. |
| Data in Use | Data being processed or accessed by applications or users; monitored through endpoint tools and DLP. |
| Control Themes (2022) | The 4 domains grouping ISO 27001:2022 controls, Organizational, People, Physical, Technological. |
| RBAC | Role-Based Access Control, limits access based on user roles and responsibilities. |
| MFA | Multi-Factor Authentication, access control using two or more verification methods. |

🔐 Hey everyone!
I wrote this blog to make the ISO/IEC 27001:2022 framework more approachable, especially for those who are navigating the shift from policy to real-world implementation.
Whether you’re a cybersecurity student, practitioner, or someone aligning your business with compliance standards, I’d love to hear your perspective.
➡️What part of the ISO framework do you find most challenging to implement?
➡️How does your organization balance technical controls with people and physical safeguards?
Let’s exchange ideas, drop your thoughts, questions, or experiences in the comments below!👇