Network Security
Understanding Threats, Attack Vectors, and Defense Mechanisms
In today’s connected world, networks are the lifelines of businesses, governments, and society. But with increased connectivity comes an equally significant risk: cyber threats that are growing more sophisticated, stealthy, and destructive. As a system or network administrator, securing a network isn’t just about installing firewalls or antivirus software; it’s about understanding the full spectrum of risks and implementing a comprehensive defense strategy.
The Modern Cybersecurity Landscape
Cybercriminals are no longer isolated hackers in basements. They operate within organized crime syndicates, nation-state cyber units, and underground marketplaces where exploits, malware, and stolen credentials are bought and sold. Their tools range from automated malware kits to AI-enhanced evasion techniques.
A successful network security strategy starts with understanding core security terms:
- Assets: Anything of value to an organization, from data to infrastructure.
- Vulnerabilities: Weaknesses that could be exploited.
- Threats: Potential dangers that could exploit vulnerabilities.
- Exploits: Mechanisms or tools used to attack vulnerabilities.
- Risk: The likelihood of a threat exploiting a vulnerability.
These concepts lay the foundation for assessing and mitigating cyber threats.
Understanding Attack Vectors
Attack vectors are the paths or means by which cybercriminals gain unauthorized access. These can be external, such as phishing emails, exposed ports, and malware laced websites, or internal, such as disgruntled employees, insecure devices, or poor password practices.
A common attack vector is a Denial of Service (DoS) attack, where an attacker overwhelms a system to render it unusable. Another frequent scenario involves internal actors accidentally leaking data via unsecured USB devices or cloud storage.
Understanding these vectors enables organizations to build defenses that anticipate, detect, and neutralize such attacks.
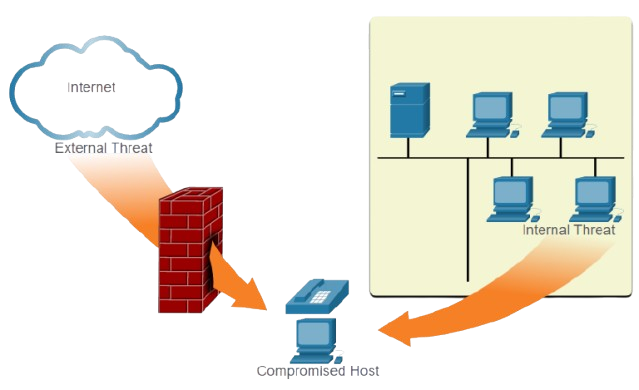
Threat Actors and Their Tools
Threat actors, often called hackers, fall into categories based on their intent:
- White Hat Hackers: Ethical hackers who find vulnerabilities to improve security.
- Black Hat Hackers: Malicious actors seeking financial or political gain.
- Gray Hat Hackers: Operating in legal gray zones, they may expose flaws but without consent.
Over time, the tools used by these actors have evolved dramatically. Tools like Metasploit for exploitation, Wireshark for packet analysis, or John the Ripper for password cracking can be used for both defense and offense.
Moreover, specialized operating systems like Kali Linux offer preloaded penetration testing tools, making them staples in both ethical hacking and cybercrime.
Malware: The Most Persistent Threat
Malware is a broad category that includes viruses, worms, Trojan horses, ransomware, spyware, and rootkits. Each operates differently:
- Viruses attach themselves to files and require human action.
- Worms self-replicate across networks.
- Trojans disguise themselves as legitimate software.
- Ransomware encrypts data and demands payment.
These tools are often delivered through phishing attacks, malicious downloads, or compromised websites.
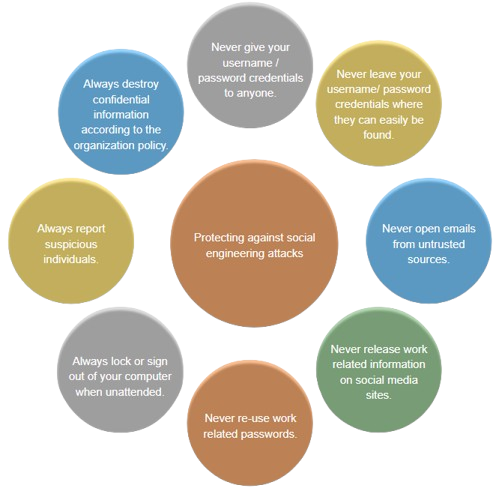
Social Engineering and Psychological Manipulation
Not all attacks rely on technical exploits. Social engineering manipulates human psychology.
Examples include:
- Phishing and Spear Phishing: Fake emails that trick users into revealing credentials.
- Baiting and Pretexting: Pretending to need data for legitimate purposes.
- Tailgating and Dumpster Diving: Gaining physical access by following an employee into a secure area.
Educating users is one of the most effective ways to combat these non-technical attacks.
Protocol and Service Vulnerabilities
Core networking protocols like ARP, DNS, DHCP, and even TCP/IP were not designed with security in mind. As such, they are vulnerable to:
- ARP Spoofing: Redirecting traffic through malicious devices.
- DNS Tunneling: Hiding data within DNS queries.
- DHCP Spoofing: Providing false configuration to redirect or disable traffic.
- TCP SYN Floods: Exploiting the three-way handshake to overload servers.
Mitigating these threats requires deep packet inspection, strict access control lists (ACLs), and frequent auditing
Defending the Network: Defense in Depth
A layered approach is critical. This means combining multiple security measures at different levels:
- Firewalls filter inbound and outbound traffic.
- Intrusion Prevention Systems (IPS) detect and block malicious activity.
- Content Security Appliances (ESA/WSA) handle email and web-based threats.
- Cryptography ensures data integrity, confidentiality, and authentication.
Using cryptographic methods like
- Hashing: MD5, SHA-1, SHA-2 for integrity
- HMAC: Adds authentication
- Encryption:
- Symmetric (AES, 3DES)
- Asymmetric (RSA, DH, ECC)
can secure communication channels and protect data at rest and in transit.
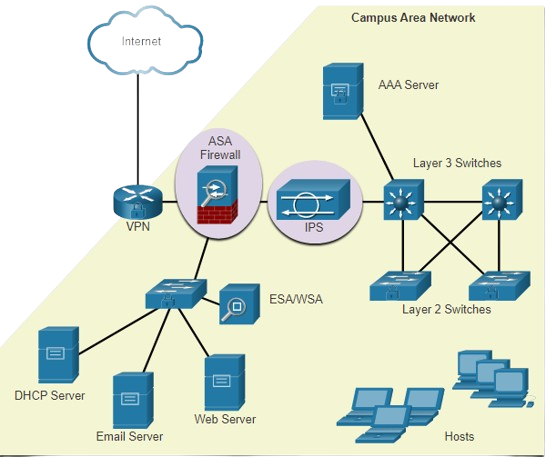
Best Practices and Final Thoughts
Security is not a product, it’s a process. Here are key practices:
- Apply software updates regularly.
- Use strong, unique passwords with multi-factor authentication.
- Educate staff about social engineering.
- Monitor logs and network traffic for anomalies.
- Perform regular vulnerability scans and penetration tests.
Understanding network security is essential for anyone working in IT. Whether you’re an administrator, a developer, or a user, knowing how data moves and where threats exist is key to building secure systems. The more informed we are, the more resilient our networks become.
Network Security
Glossary of Key Terms
| Term | Definition |
|---|---|
| Asset | Anything of value to the organization, including data, people, devices, or infrastructure. |
| Vulnerability | A weakness in a system or design that could be exploited by a threat. |
| Threat | A potential danger that could exploit a vulnerability. |
| Exploit | A method or tool that takes advantage of a vulnerability. |
| Mitigation | Actions taken to reduce the risk or impact of a threat. |
| Risk | The likelihood and potential impact of a threat exploiting a vulnerability. |
| Threat Actor | Any person, device, or group that causes or attempts an attack (includes hackers, insiders). |
| White Hat Hacker | An ethical hacker who uses skills to find and report vulnerabilities legally. |
| Black Hat Hacker | A malicious hacker who exploits vulnerabilities for personal gain or disruption. |
| Gray Hat Hacker | Someone who may violate ethical or legal standards but without malicious intent. |
| Penetration Testing | The practice of simulating cyberattacks to test a system’s defenses. |
| Man-in-the-Middle (MITM) | An attack where the threat actor intercepts and possibly alters communication between two parties. |
| Denial of Service (DoS) | An attack designed to make a system or network unavailable to users. |
| Malware | Malicious software designed to damage, exploit, or gain unauthorized access to systems. |
| Trojan Horse | Malware disguised as legitimate software to trick users into installing it. |
| Ransomware | Malware that encrypts data and demands payment to restore access. |
| Sniffer | A tool that captures network traffic for analysis (can be used ethically or maliciously). |
| Rootkit | Malware that gains root-level access and hides its presence from the system. |
| Social Engineering | Psychological manipulation to trick people into giving up sensitive information. |
| Phishing | Fraudulent email or messages pretending to be from trustworthy sources to steal data. |
| Buffer Overflow | An attack that overflows memory buffers to crash or hijack systems. |
| TCP SYN Flood | A DoS attack exploiting the TCP handshake process to exhaust server resources. |
| DNS Tunneling | A method of encoding data in DNS queries/responses to bypass security mechanisms. |
| HMAC | A type of hash-based message authentication code using a secret key. |
| Symmetric Encryption | Encryption where the same key is used to both encrypt and decrypt data. |
| Asymmetric Encryption | Uses a public and private key pair for encryption and decryption. |
| Firewall | A security device that filters network traffic based on configured rules. |
| IPS/IDS | Systems designed to detect (IDS) or prevent (IPS) intrusions and attacks. |
| CIA Triad | The three pillars of information security: Confidentiality, Integrity, Availability. |
5
2
votes
Article Rating
Subscribe
1 Comment
Oldest
Newest
Most Voted
Inline Feedbacks
View all comments
Jean Claude Munyakazi
7 months ago
0
